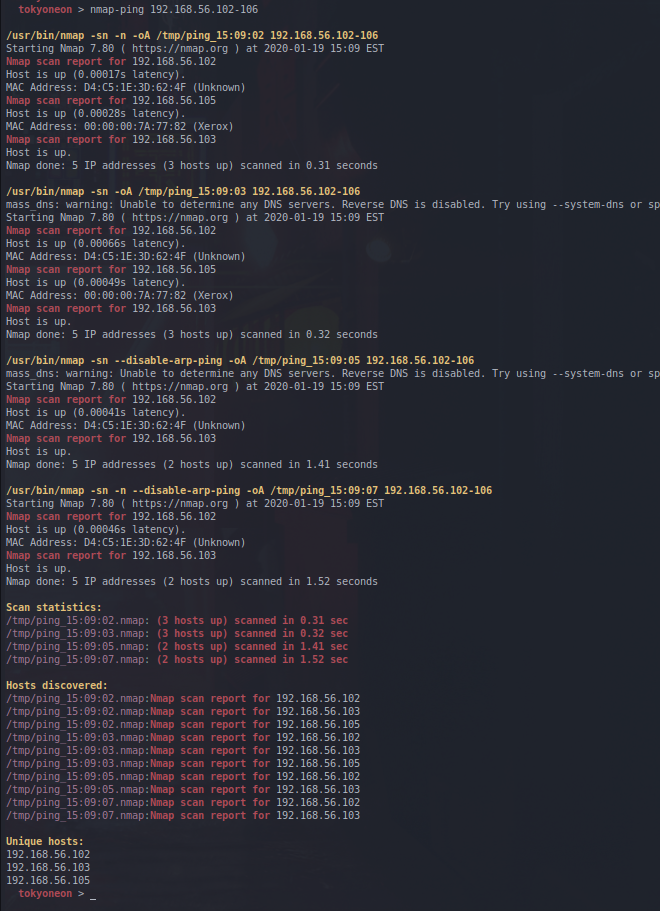
As part of my preparation for the eCPPT exam, I created this simple script to iterate though various types of ping switches. The eCPPT dedicates a lot of time to remote host and firewall configuration enumeration. While one server might respond to a particular ping method, another server may not.
nmap-ping ()
{
rm /tmp/ping_* > /dev/null 2>&1;
uniquehosts="/tmp/ping_$(date +%T).txt";
pings=("-sn -n" "-sn" "-sn --disable-arp-ping" "-sn -n --disable-arp-ping");
function print ()
{
echo -e "\n\033[1;33m$1\033[0;39m"
};
for ping in "${pings[@]}";
do
d="$(date "+%T")";
nmap_cmd="/usr/bin/nmap $ping -oA /tmp/ping_$d ${@:1}";
print "$nmap_cmd";
eval "$nmap_cmd" | grep --color=always -C50 'Nmap scan report for';
sleep 1.1;
done;
print "Scan statistics:";
grep --color=always -ioP '(?<=addresses).*?(?=onds)' /tmp/ping_*.nmap;
print "Hosts discovered:";
grep --color=always 'Nmap scan report for' /tmp/ping_*.nmap | sort -n;
print "Unique hosts:";
awk '/scan report for/{print $5}' /tmp/ping_*.nmap | sort -u | tee "$uniquehosts"
}